
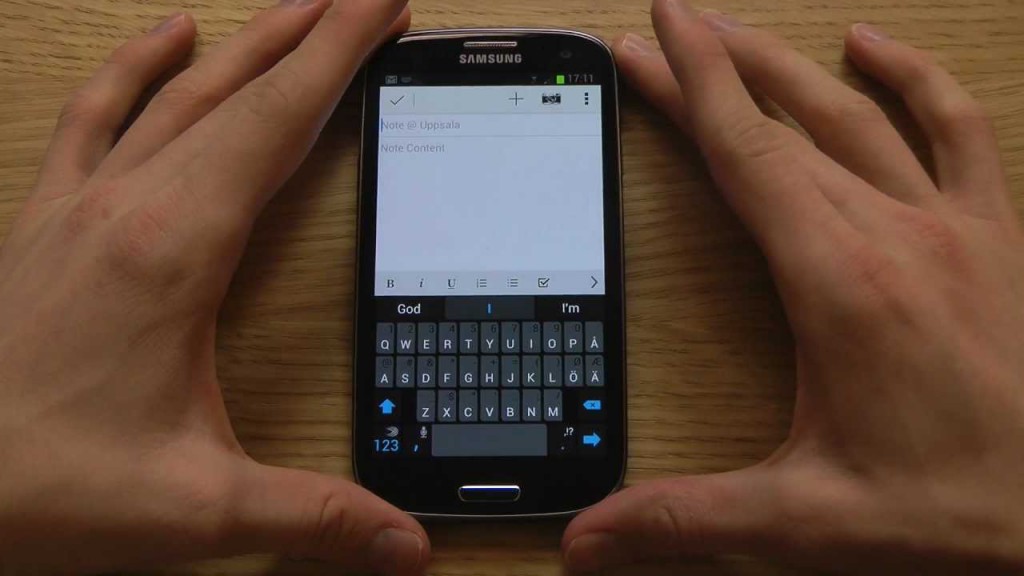
Samsung, one of the most beloved smartphone out there, and SwiftKey, one of the best keyboard app for Android, when they’re put together it sounds like a great combination, doesn’t it? Actually, it’s not!
A security flaw in the SwiftKey keyboards pre-installed on Samsung smartphones is leaving at least 600 million devices vulnerable to hackers including the new Samsung Galaxy S6. The exploit was recently demonstrated at the Black Hat security conference in London by Ryan Welton, a researcher with security firm NowSecure. NowSecure, found that the pre-installed SwiftKey app can be tricked to download language pack updates over a unencrypted connection in plain text. Thus in the presence of language packs, malicious code can be injected to take control of the smartphone.
The flaw allows a hacker to remotely:
1) Access sensors and resources like GPS, camera and microphone.
2) Secretly install a malicious app(s) without the user knowing.
3) Tamper with how other apps work or how the phone works.
4) Eavesdrop on incoming/outgoing messages or voice calls.
5) Give an attempt to access sensitive personal data like pictures and text messages.
And the scary thing is hackers can exploit the vulnerability even when the SwiftKeykeyboard is not used as the default keyboard.
There are millions of Samsung devices with SwiftKey keyboard, still vulnerable via this loophole. The list of affected devices includes Galaxy S6, Galaxy S5, Galaxy S4 and Galaxy S4 Mini, however, NowSecure cautions that this is not an all-inclusive list of impacted devices.
There is no way one can uninstall SwiftKey from the Samsung’s Galaxy range of devices since the app has been whitelisted and deemed to be native. The keyboard which cannot be disabled or uninstalled allows hackers easy access to users’ devices. However, you can always remove a system app simply by rooting your device. If you don’t want to root your device wait till there is a patch released for the Samsung phones. If you own a Samsung device and are concerned about this bug, NowSecure advises that you do not use insecure Wi-Fi networks and do not update your language packages in the mean time.















![Best Gaming Laptops in Nepal 2024 [Updated] Best Gaming Laptops in Nepal 2023 - June Update](https://cdn.gadgetbytenepal.com/wp-content/uploads/2023/04/Best-Gaming-Laptops-in-Nepal-2023-June-Update.jpg)




![Best Mobile Phones Under Rs. 15,000 in Nepal [Updated] Best Phones Under 15000 in Nepal 2024 Budget Smartphones Cheap Affordable](https://cdn.gadgetbytenepal.com/wp-content/uploads/2024/03/Best-Phones-Under-15000-in-Nepal-2024.jpg)
![Best Mobile Phones Under Rs. 20,000 in Nepal [Updated] Best Mobile Phones Under NPR 20000 in Nepal 2023 Updated Samsung Xiaomi Redmi POCO Realme Narzo Benco](https://cdn.gadgetbytenepal.com/wp-content/uploads/2024/01/Best-Phones-Under-20000-in-Nepal-2024.jpg)
![Best Mobile Phones Under Rs. 30,000 in Nepal [Updated]](https://cdn.gadgetbytenepal.com/wp-content/uploads/2023/12/Best-Phones-Under-30000-in-Nepal-2024.jpg)
![Best Mobile Phones Under Rs. 40,000 in Nepal [Updated] Best Phones Under 40000 in Nepal 2024 Smartphones Mobile Midrange](https://cdn.gadgetbytenepal.com/wp-content/uploads/2024/02/Best-Phones-Under-40000-in-Nepal-2024.jpg)
![Best Mobile Phones Under Rs. 50,000 in Nepal [Updated] Best Phones Under 50000 in Nepal 2024 Smartphones Midrange](https://cdn.gadgetbytenepal.com/wp-content/uploads/2024/02/Best-Phones-Under-50000-in-Nepal-2024.jpg)
![Best Flagship Smartphones To Buy In Nepal [Updated] Best Smartphones in Nepal 2024 Flagship Premium Samsung Apple iPhone Xiaomi OnePlus Honor](https://cdn.gadgetbytenepal.com/wp-content/uploads/2023/09/Best-Smartphones-in-Nepal-2024.jpg)