
Researchers have found a fake Netflix app guilty of phishing, stealing credentials, and other malicious activities. The malware made to look like Netflix on the Google Play Store was promising free subscriptions. Let’s learn more about the malicious activities of FlixOnline, the fake Netflix app.
Flixonline, the fake Netflix app
Check Point Research team discovered malware hidden inside FlixOnline. The app itself was disguised to look like Netflix. It cheated users by promising up to 2 months of premium Netflix subscription for free. However, once downloaded, the app used to monitor user’s WhatsApp activities.

Access to WhatsApp notifications
The app would ask for multiple permission during the initial startup, one of which was notification access. When permitted, it allowed the app to dig into your notifications and even carry out quick actions on your behalf.
It would hide all incoming notifications out of the user’s sight and then carry out quick actions like “dismiss”, “reply”, and whatever is compatible with that particular notification.
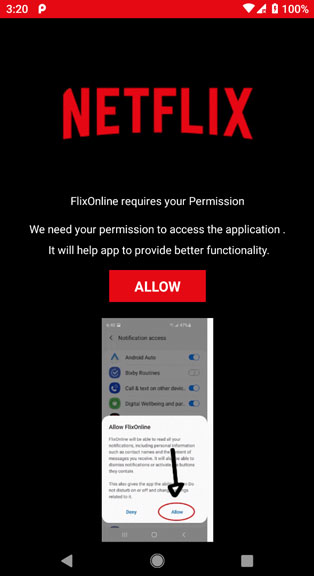
FlixOnline was found manipulating WhatsApp notifications. The app would even detect incoming messages and send automatic replies from the remote command and control (C&C) server. The message contained a link to download the fake app.
“2 Months of Netflix Premium Free at no cost For REASON OF QUARANTINE (CORONA VIRUS)* Get 2 Months of Netflix Premium Free anywhere in the world for 60 days. Get it now HERE https://bit[.]ly/3bDmzUw.”
So, if you have received any message recently like the one above from your WhatsApp contact, it’s because of a FlixOnline-infected device (the fake Netflix app). Such activity would allow the app to multiply.
Malicious activities of the fake Netflix app: Flixonline
Once all the permissions were granted, the app would hide all its icons from the device to avoid removal. It would still be in contact with the remote C&C server—the server used to provide updates to the app to carry out further activities.
And there’s much more to it. The app also requested overlay permission. Though there was no reported case of such an incident, the app was well capable of carrying out a phishing attempt. This could have been done by simply pushing a fake “Login” page on top of other apps.
Damage done
According to the researchers, the app had over 500 downloads on the Google Play Store in the span of 2 months. Google has removed the app from the Play Store upon being notified by the research team. Still, the app could remain hidden on the user’s device. If you still have the app on your phone, you should remove it immediately and change all your password.
How to be safe from such apps?
This recent incident is not something new. Hackers have been fooling people into installing malware by alluring them with free subscriptions to premium apps. When you receive such offers in your inbox, it might be tempting to click on them, especially when you receive them from a trusted contact. However, it’s important to know that hackers can manipulate one’s virtual identity to trick others into its trap. So double-check every incoming message and link even if it’s from the people you trust.
- Meanwhile, check out our review of the Galaxy A72.















![Best Ultrabooks To Buy in Nepal 2024 [Updated] Best Ultrabook Laptops in Nepal 2023 - June Update](https://cdn.gadgetbytenepal.com/wp-content/uploads/2023/04/Best-Ultrabook-Laptops-in-Nepal-2023-June-Update.jpg)
![Best Gaming Laptops in Nepal 2024 [Updated] Best Gaming Laptops in Nepal 2023 - June Update](https://cdn.gadgetbytenepal.com/wp-content/uploads/2023/04/Best-Gaming-Laptops-in-Nepal-2023-June-Update.jpg)


![Best Mobile Phones Under Rs. 15,000 in Nepal [Updated] Best Phones Under 15000 in Nepal 2024 Budget Smartphones Cheap Affordable](https://cdn.gadgetbytenepal.com/wp-content/uploads/2024/03/Best-Phones-Under-15000-in-Nepal-2024.jpg)
![Best Mobile Phones Under Rs. 20,000 in Nepal [Updated] Best Mobile Phones Under NPR 20000 in Nepal 2023 Updated Samsung Xiaomi Redmi POCO Realme Narzo Benco](https://cdn.gadgetbytenepal.com/wp-content/uploads/2024/01/Best-Phones-Under-20000-in-Nepal-2024.jpg)
![Best Mobile Phones Under Rs. 30,000 in Nepal [Updated]](https://cdn.gadgetbytenepal.com/wp-content/uploads/2023/12/Best-Phones-Under-30000-in-Nepal-2024.jpg)
![Best Mobile Phones Under Rs. 40,000 in Nepal [Updated] Best Phones Under 40000 in Nepal 2024 Smartphones Mobile Midrange](https://cdn.gadgetbytenepal.com/wp-content/uploads/2024/02/Best-Phones-Under-40000-in-Nepal-2024.jpg)
![Best Mobile Phones Under Rs. 50,000 in Nepal [Updated] Best Phones Under 50000 in Nepal 2024 Smartphones Midrange](https://cdn.gadgetbytenepal.com/wp-content/uploads/2024/02/Best-Phones-Under-50000-in-Nepal-2024.jpg)
![Best Flagship Smartphones To Buy In Nepal [Updated] Best Smartphones in Nepal 2024 Flagship Premium Samsung Apple iPhone Xiaomi OnePlus Honor](https://cdn.gadgetbytenepal.com/wp-content/uploads/2023/09/Best-Smartphones-in-Nepal-2024.jpg)